Please Note: This article is valid for EventReporter 9.x / MWAgent 5.x and lower and describes, how to set the filters to get only logon, failed logon and lockout events.
The scenario is, that we need to monitor the behavior of users logging into machines, as well as failing or being locked out, due to bad inserted passwords. All those events should be written into a text file with a unique message that indicates to us what has happened. We need only one ruleset and one service for this. The service would be the EventLog Monitor. In the ruleset, we need 3 separate rules with each having one Action, the Write to File Action. The basic setup should look like this:
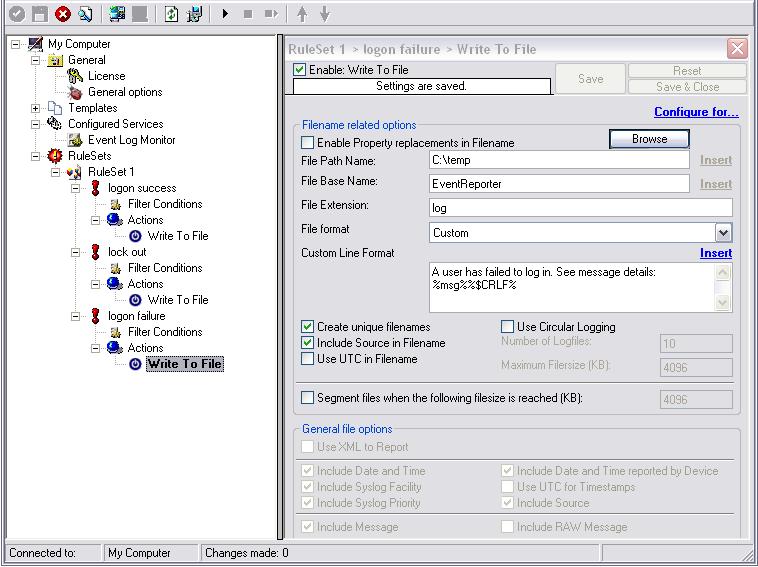
Image 1: Basic Setup
Now we will get to the core part of this setup. The filters. This will be a little bit complex, as there are a lot of possibilities when it comes to monitoring logon events. We need to monitor the events with the following IDs:
- Event ID: 528 – Successful Logon
- Event ID: 529 – Logon Failure: Unknown user name or bad password
- Event ID: 530 – Logon Failure: Account logon time restriction violation
- Event ID: 531 – Logon Failure: Account currently disabled
- Event ID: 532 – Logon Failure: The specified user account has expired
- Event ID: 533 – Logon Failure: User not allowed to logon at this computer
- Event ID: 534 – Logon Failure: The user has not been granted the requested logon type at this machine
- Event ID: 535 – Logon Failure: The specified account’s password has expired
- Event ID: 536 – Logon Failure: The NetLogon component is not active
- Event ID: 537 – Logon Failure: An unexpected error occurred during logon
- Event ID: 539 – Logon Failure: Account locked out
We need to split up these events for the different rules we created before. To summarize it, we need the following packages:
- Logon Success: Event ID 528
- Logon Failure: Event ID 529 – 537
- Account Lockout: Event ID 539
There are a lot of Events available for logon failure. So we have to consider all the events that would fit. If some events do not fit for your account policy auditing, then simply leave them out. With this information in mind, we set up the filters. The first two filter will be for “Successful Logon” and “Account Lockout”. We use the “AND”-Operator and filter for the Event ID. This looks as follows:
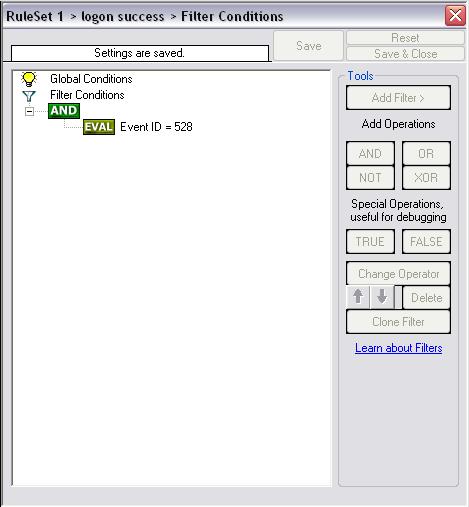
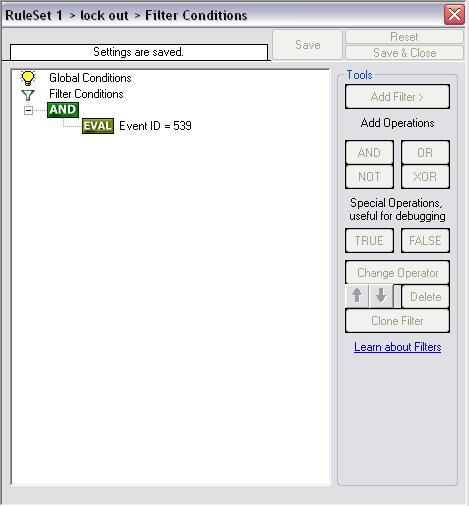
Image 2 and 3: Filter for “Successful Logon” and “Account Lockout”
The last filter for “Logon Failure” looks a bit different, as we have multiple conditions that we need to check. Therefore we need a different Operator. We will take the “OR”-Operator as this is the most suitable. It will evaluate to true once one of the multiple conditions is true. So the same Action (writing a message to a textfile that tells us, that a login has failed) can be performed for multiple events. In contrary, the “AND”-Operator needs all conditions to be true to process the Event, else the Action will not be carried out. The filter should look like this:
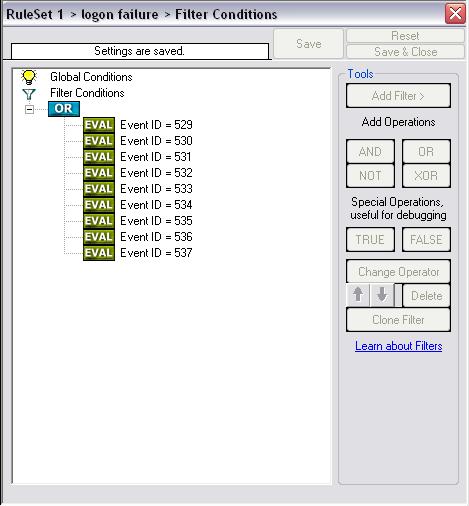
Image 4: Filter for “Logon Failure”
The last thing we have to do is to set the messages that should be written into the textfile. Therefore go to each “Write to File”-Action and set the “File Format” to “Custom”. Then you can edit the message to whatever you like. I chose these messages for my example:
- A User has successfully logged in, see message details: %msg%%$CRLF%
- A User has been locked out. See messages details: %msg%%$CRLF%
- A User has failed to log in. See message details: %msg%%$CRLF%
These messages give you directly a comment about the event that happened and show you the original message, which holds the information about the user, machine and message details. The configuration for one of those Actions could look like this:
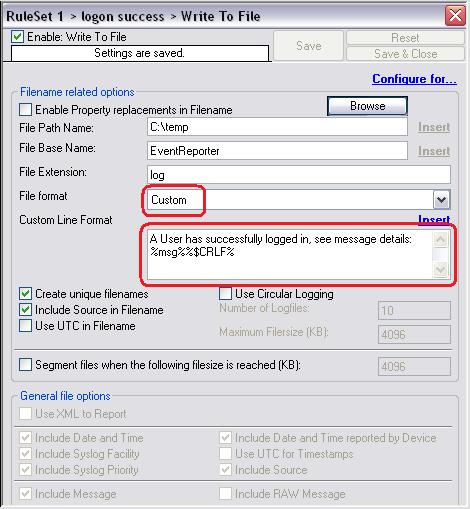
Image 5: Settings for “Write to File”-Action
Please Note: Every “Write to File”-Action needs to write its messages into the same file. Else, you will have separate files for all three kinds of messages. If writing to the same file, a message will be written one after another, so there will not be any overlapping with the messages.
You could also make this message a bit more detailed by including the timestamp and the name of the machine on which the Event happened. Then it could look like this:
- %timereported%, %Param0%, %Param1%, %Param5%, Logon Failure%$CRLF%
This would result in the following message:
2008-10-14 09:24:33, Username, Domain, Workstation, Logon Failure
The message now contains the complete timestamp with date and time, the name of the Domain for which the Event applies, the Workstation name from which the message originates and “Logon Failure” as comment to what happened. We have to do this in a fixed way, as we do not have this information automatically parsed from the Event message. If you want to have the detailed description for the Event you can either add the complete message with %msg% or parse out the information before writing it and put it into a custom property with the “Post-Processing”-Action (only available in MonitorWare Agent Professional and Enterprise).
This is all that needs to be done for having all events for Successful Logon, Logon Failure and Account Lockout written into a textfile. If you have any remarks, suggestions or questions to this article, please send a email to our Support Team.
